- Table of contents
- IKEv2 Configuration Profile for Apple iOS 8 and newer
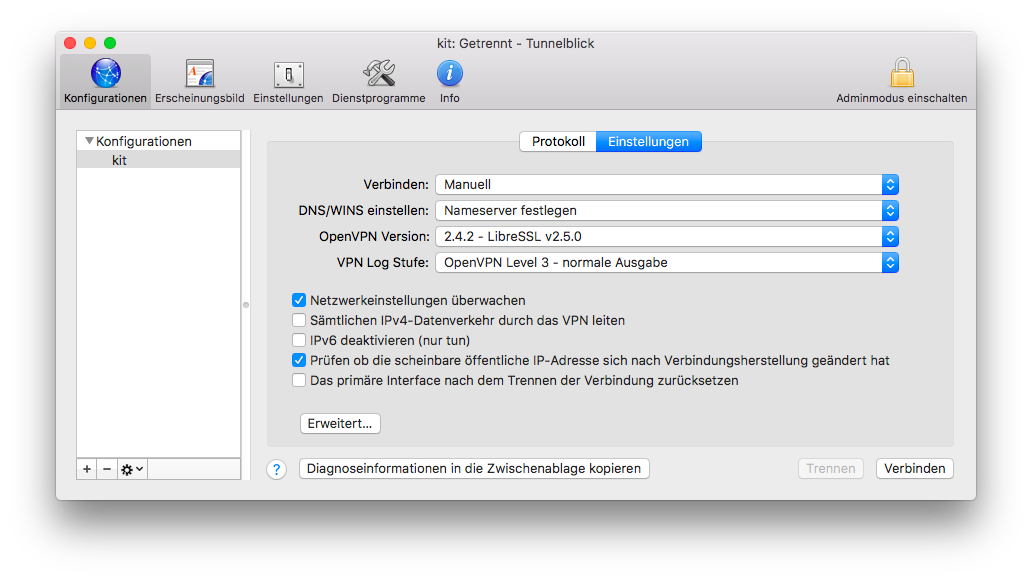
Nearly perfect I have a specific usage case - I work in a multiplatform environment in which I work on the Mac and on the PC. I don't want to keep changing physical keyboards, so despite the fact that the two physical machines are next to eachother beneath my desk, I use remote desktop to view and operate the PC while working on the Mac. Set up a VPN connection on Mac. To connect to a virtual private network (VPN), you need to enter configuration settings in Network preferences. These settings include the VPN server address, account name, and any authentication settings, such as a password. For Interface, select VPN from the drop-down menu. For VPN Type, select IKEv2. In the Service Name field, type any name you want. We recommend that you name the service NordVPN (IKEv2). The settings for the new VPN connection will now be displayed. In the Server Address and Remote ID fields, type the hostname of a NordVPN server. Select the VPN option as the Interface. Select PPTP as the VPN Type and enter a Service Name. Click on the Create button. Enter the VPN server name or IP to the Server Address textbox and the VPN user name to the Account Name field. Click the Authentication Settings button and enter your VPN account access password. Click the OK button.
While iOS 8 introduced native IKEv2 support, the VPN application's GUI was initially not updated to allow configuration of such connections on the devices themselves. Therefore, it was required to create IKEv2 connections with custom configuration profiles. Principle for windows 10.
Since iOS 9 IKEv2 connections may be configured in the GUI. But it is still possible to configure VPN connections with profiles (offering settings that are not available in the GUI).
Such profiles can be created manually, or you can use Apple Configurator or Apple Profile Manager.
You can adjust the following templates to your setup and then send it to your device(s) via email or provide it via HTTP. In order for the iOS mail client to install the profile, the file name of the attachment must end in .mobileconfig and the content type should be application/octet-stream (Thunderbird seems to use text/html, which will not work).
Format my book for mac. Several notes to the configuration keys are provided as comments in the template files below, the official documentation can be found at developer.apple.com. Apple m7803 keyboard.
Mac OS X 10.11 and newer support IKEv2. Earlier versions only support IKEv1.
Known Issues¶
- ASN.1 Distinguished Names can't be used as identities because the client currently sends them as identities of type FQDN.
- If EAP authentication is used a username has to be configured in the profile, there is no prompt during installation (or later) if it is not set. The password is optional though, if it is not set in the profile it can be entered during installation.This has been fixed with iOS 9.
- The client requests a virtual IPv6 address and sends IPv6 traffic selectors. Unfortunately, these selectors are invalid. The end address is sent as
00ff:00ff:00ff:00ff:00ff:00ff:00ff:00ffinstead offfff:ffff:ffff:ffff:ffff:ffff:ffff:ffff. So IPv6 can't really be used and if the responder can't handle such a proposal (like e.g. Windows Server) the connection will fail altogether (it seems not possible to disable IPv6 on the client via configuration profile).This has been fixed with iOS 8.3.
Authentication options¶
Id Remoto Vpn Mac Download
Imageranger pro 1 5 4 1267 download free. The client and server authentication is determined by the following options (more details can be found in comments in the templates below):
- AuthenticationMethod = Certificate
In all these variants the server is authenticated with a certificate. The ServerCertificateIssuerCommonName and ServerCertificateCommonName options are used to verify the server certificate.
- ExtendedAuthEnabled = 0 and PayloadCertificateUUID set
The client is authenticated using a certificate using the pubkey authentication method.
- ExtendedAuthEnabled = 1
- PayloadCertificateUUID set
The client is authenticated with a certificate using EAP-TLS. Mac mini keyboard case.
- PayloadCertificateUUIDnot set
The client is authenticated with a username/password-based EAP method using EAP-MSCHAPv2. Use of other EAP types (EAP-MD5, EAP-GTC for example) will see an IKE AUTH failure asking to use EAP-MSCHAPv2 (i.e. tested on IOS 9). The credentials can be configured with AuthName and AuthPassword.
- PayloadCertificateUUID set
- ExtendedAuthEnabled = 0 and PayloadCertificateUUID set
- AuthenticationMethod = SharedSecret
Uses PSK authentication for client and server. The PSK can be configured with the SharedSecret option.
EAP authentication (base template)¶
This configuration is compatible to the Windows 7 EAP server configuration.
Id Remoto Vpn Mac Os
Certificate authentication¶
This configuration is compatible to the Windows 7 machine certificate server configuration.
Only the differences to the above configuration are shown.
EAP-TLS authentication¶
This configuration is compatible to the Windows 7 user certificate server configuration.
This is basically the same as the certificate configuration above, but with ExtendedAuthEnabled activated.
Pre-shared key (PSK) authentication¶
Is is also possible to use PSKs for authentication.
Enable On-Demand VPN¶
It is possible to automatically trigger an VPN-Connect if needed. This example show rules, which will disconnect the tunnel when connected to a specific WiFi SSID (MySSID) and establishes a tunnel when domain name resolution of specific domains fail (*.internal.mydomain.com).
For more details have a look at Apples Configuration Profile Reference
Questo articolo consente di risolvere i problemi di connettività da punto a sito da Mac OS X tramite il client VPN nativo e IKEv2.This article helps you troubleshoot Point-to-Site connectivity issues from Mac OS X using the native VPN client and IKEv2.Il client VPN in Mac per IKEv2 è molto semplice e non consente un livello elevato di personalizzazione.The VPN client in Mac for IKEv2 is very basic and does not allow for much customization.È necessario controllare solo quattro impostazioni:There are only four settings that need to be checked:
- Server AddressServer Address
- ID remotoRemote ID
- ID localeLocal ID
- Impostazioni di autenticazioneAuthentication Settings
- Versione del sistema operativo: 10.11 o successivaOS Version (10.11 or higher)
Risolvere i problemi di autenticazione basata su certificatiTroubleshoot certificate-based authentication
Controllare le impostazioni del client VPN.Check the VPN client settings.Passare a Network Setting (Impostazioni di rete) premendo Comando + Maiusc e quindi digitare 'VPN' per controllare le impostazioni del client VPN.Go to the Network Setting by pressing Command + Shift, and then type 'VPN' to check the VPN client settings.Nell'elenco fare clic sulla voce VPN che deve essere esaminata.From the list, click the VPN entry that needs to be investigated.
Verificare che l'indirizzo del server sia il nome di dominio completo e che includa cloudapp.net.Verify that the Server Address is the complete FQDN and includes the cloudapp.net.
L'ID remoto deve essere uguale all'indirizzo del server (nome di dominio completo del gateway).The Remote ID should be the same as the Server Address (Gateway FQDN).
L'ID locale deve essere uguale al soggetto del certificato client.The Local ID should be the same as the Subject of the client certificate.
Fare clic su Authentication Settings (Impostazioni di autenticazione) per aprire la pagina Authentication Settings (Impostazioni di autenticazione).Click on Authentication Settings to open the Authentication Settings page.
Verificare che Certificate (Certificato) sia stato selezionato dall'elenco a discesa.Verify that Certificate is selected from the dropdown.
Fare clic sul pulsante Select (Seleziona) e verificare che sia stato selezionato il certificato corretto.Click the Select button and verify that the correct certificate is selected.Fare clic su OK per salvare le modifiche.Click OK to save any changes.
Risolvere i problemi di autenticazione di nome utente e passwordTroubleshoot username and password authentication
Controllare le impostazioni del client VPN.Check the VPN client settings.Passare a Network Setting (Impostazioni di rete) premendo Comando + Maiusc e quindi digitare 'VPN' per controllare le impostazioni del client VPN.Go to the Network Setting by pressing Command + Shift, and then type 'VPN' to check the VPN client settings.Nell'elenco fare clic sulla voce VPN che deve essere esaminata.From the list, click the VPN entry that needs to be investigated.
Verificare che l'indirizzo del server sia il nome di dominio completo e che includa cloudapp.net.Verify that the Server Address is the complete FQDN and includes the cloudapp.net.
L'ID remoto deve essere uguale all'indirizzo del server (nome di dominio completo del gateway).The Remote ID should be the same as the Server Address (Gateway FQDN).
Il campo Local ID (ID locale) può essere vuoto.The Local ID can be blank.
Fare clic sul pulsante Authentication Setting (Impostazioni di autenticazione) e verificare che 'Username' (Nome utente) sia stato selezionato nell'elenco a discesa.Click the Authentication Setting button and verify that 'Username' is selected from the dropdown.
Verificare che siano state immesse le credenziali corrette.Verify that the correct credentials are entered.
Passaggi aggiuntiviAdditional steps
Se si segue la procedura precedente e tutto viene configurato correttamente, scaricare Wireshark ed eseguire un'acquisizione pacchetti.If you try the previous steps and everything is configured properly, download Wireshark and perform a packet capture.
Id Remoto Vpn Mac Download
Imageranger pro 1 5 4 1267 download free. The client and server authentication is determined by the following options (more details can be found in comments in the templates below):
- AuthenticationMethod = Certificate
In all these variants the server is authenticated with a certificate. The ServerCertificateIssuerCommonName and ServerCertificateCommonName options are used to verify the server certificate.
- ExtendedAuthEnabled = 0 and PayloadCertificateUUID set
The client is authenticated using a certificate using the pubkey authentication method.
- ExtendedAuthEnabled = 1
- PayloadCertificateUUID set
The client is authenticated with a certificate using EAP-TLS. Mac mini keyboard case.
- PayloadCertificateUUIDnot set
The client is authenticated with a username/password-based EAP method using EAP-MSCHAPv2. Use of other EAP types (EAP-MD5, EAP-GTC for example) will see an IKE AUTH failure asking to use EAP-MSCHAPv2 (i.e. tested on IOS 9). The credentials can be configured with AuthName and AuthPassword.
- PayloadCertificateUUID set
- ExtendedAuthEnabled = 0 and PayloadCertificateUUID set
- AuthenticationMethod = SharedSecret
Uses PSK authentication for client and server. The PSK can be configured with the SharedSecret option.
EAP authentication (base template)¶
This configuration is compatible to the Windows 7 EAP server configuration.
Id Remoto Vpn Mac Os
Certificate authentication¶
This configuration is compatible to the Windows 7 machine certificate server configuration.
Only the differences to the above configuration are shown.
EAP-TLS authentication¶
This configuration is compatible to the Windows 7 user certificate server configuration.
This is basically the same as the certificate configuration above, but with ExtendedAuthEnabled activated.
Pre-shared key (PSK) authentication¶
Is is also possible to use PSKs for authentication.
Enable On-Demand VPN¶
It is possible to automatically trigger an VPN-Connect if needed. This example show rules, which will disconnect the tunnel when connected to a specific WiFi SSID (MySSID) and establishes a tunnel when domain name resolution of specific domains fail (*.internal.mydomain.com).
For more details have a look at Apples Configuration Profile Reference
Questo articolo consente di risolvere i problemi di connettività da punto a sito da Mac OS X tramite il client VPN nativo e IKEv2.This article helps you troubleshoot Point-to-Site connectivity issues from Mac OS X using the native VPN client and IKEv2.Il client VPN in Mac per IKEv2 è molto semplice e non consente un livello elevato di personalizzazione.The VPN client in Mac for IKEv2 is very basic and does not allow for much customization.È necessario controllare solo quattro impostazioni:There are only four settings that need to be checked:
- Server AddressServer Address
- ID remotoRemote ID
- ID localeLocal ID
- Impostazioni di autenticazioneAuthentication Settings
- Versione del sistema operativo: 10.11 o successivaOS Version (10.11 or higher)
Risolvere i problemi di autenticazione basata su certificatiTroubleshoot certificate-based authentication
Controllare le impostazioni del client VPN.Check the VPN client settings.Passare a Network Setting (Impostazioni di rete) premendo Comando + Maiusc e quindi digitare 'VPN' per controllare le impostazioni del client VPN.Go to the Network Setting by pressing Command + Shift, and then type 'VPN' to check the VPN client settings.Nell'elenco fare clic sulla voce VPN che deve essere esaminata.From the list, click the VPN entry that needs to be investigated.
Verificare che l'indirizzo del server sia il nome di dominio completo e che includa cloudapp.net.Verify that the Server Address is the complete FQDN and includes the cloudapp.net.
L'ID remoto deve essere uguale all'indirizzo del server (nome di dominio completo del gateway).The Remote ID should be the same as the Server Address (Gateway FQDN).
L'ID locale deve essere uguale al soggetto del certificato client.The Local ID should be the same as the Subject of the client certificate.
Fare clic su Authentication Settings (Impostazioni di autenticazione) per aprire la pagina Authentication Settings (Impostazioni di autenticazione).Click on Authentication Settings to open the Authentication Settings page.
Verificare che Certificate (Certificato) sia stato selezionato dall'elenco a discesa.Verify that Certificate is selected from the dropdown.
Fare clic sul pulsante Select (Seleziona) e verificare che sia stato selezionato il certificato corretto.Click the Select button and verify that the correct certificate is selected.Fare clic su OK per salvare le modifiche.Click OK to save any changes.
Risolvere i problemi di autenticazione di nome utente e passwordTroubleshoot username and password authentication
Controllare le impostazioni del client VPN.Check the VPN client settings.Passare a Network Setting (Impostazioni di rete) premendo Comando + Maiusc e quindi digitare 'VPN' per controllare le impostazioni del client VPN.Go to the Network Setting by pressing Command + Shift, and then type 'VPN' to check the VPN client settings.Nell'elenco fare clic sulla voce VPN che deve essere esaminata.From the list, click the VPN entry that needs to be investigated.
Verificare che l'indirizzo del server sia il nome di dominio completo e che includa cloudapp.net.Verify that the Server Address is the complete FQDN and includes the cloudapp.net.
L'ID remoto deve essere uguale all'indirizzo del server (nome di dominio completo del gateway).The Remote ID should be the same as the Server Address (Gateway FQDN).
Il campo Local ID (ID locale) può essere vuoto.The Local ID can be blank.
Fare clic sul pulsante Authentication Setting (Impostazioni di autenticazione) e verificare che 'Username' (Nome utente) sia stato selezionato nell'elenco a discesa.Click the Authentication Setting button and verify that 'Username' is selected from the dropdown.
Verificare che siano state immesse le credenziali corrette.Verify that the correct credentials are entered.
Passaggi aggiuntiviAdditional steps
Se si segue la procedura precedente e tutto viene configurato correttamente, scaricare Wireshark ed eseguire un'acquisizione pacchetti.If you try the previous steps and everything is configured properly, download Wireshark and perform a packet capture.
Filtrare in base a isakmp ed esaminare i pacchetti IKE_SA.Filter on isakmp and look at the IKE_SA packets.È possibile esaminare i dettagli della proposta SA in Payload: Security Association (Payload: associazione di sicurezza).You should be able to look at the SA proposal details under the Payload: Security Association.
Verificare che il client e il server dispongano di un set comune.Verify that the client and the server have a common set.
Se non è presente alcuna risposta server sulle tracce di rete, verificare di aver abilitato il protocollo IKEv2 nella pagina di configurazione del gateway di Azure nel sito Web portale di Azure.If there is no server response on the network traces, verify you enabled IKEv2 protocol on the Azure Gateway Configuration page on the Azure portal website.
Passaggi successiviNext steps
Per altre informazioni, contattare il supporto tecnico Microsoft.For additional help, see Microsoft Support.